Part I |

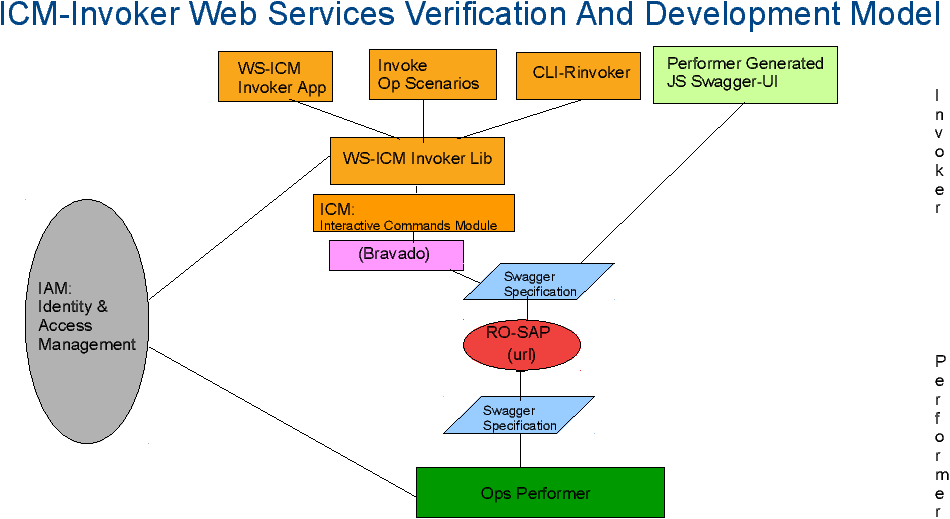
Figure 1: Swagger Based ICM Web Services Invoker Model
The Web-Services Validation Tools assume that a correct Swagger Specification is available. These tools do not focus on validating the service specification – there are a variety of tools available for validation of the swagger specifications, that is a different topic. These tools focus on validating the service based on its assumed correct specification.
These tools are invocation tools. They operate purely as the client side and other than verification and use of the service their scope does not extent to the server side (performers).
These tools are purely python based and they are purely Open Source (FOSS, Libre-Halaal). The python packages are available at PyPi and the complete source code is available at github.
You can think of these tools as a layer on top of
Bravado – https://bravado.readthedocs.io/en/stable/,
https://github.com/Yelp/bravado.
Bravado ingests the swagger service specification in json or yaml and maps it to python on the fly. Bravado is a complete replacement to swagger codegen – the traditional code generation phase is eliminated. The Web-Services Validation Tools then create a higher level of convenience for invoking the operations specified in the service specification.
The Web-Services Validation Tools fall into two broad categories of:
Based on a given a swagger specification, rinvoker.py maps the json/yaml specification to python (using Bravado) and then python functions corresponding to remote-operation invocations are exposed as command-line using the ICM package (Interactive Command Modules).
All of this happens on the fly. Given a service-specification and a base service url, all operations become available for invocation at command line.
Pointers to examples and additional details are provided below.
In many situations the command-line interface may not be adequate for operations invocations as the parameters syntax may be complex, and as the results syntax may complex and as operation invocations sequences may be chained or interdependent. For such situation, a high level python interface called Operation-Scenarios (opScn) is provided.
You can then customize remote operation invocations as concrete scenarios (opScn) specifications.
Pointers to examples and additional details are provided below.
If you don’t have Python 2.7 already installed, execute the following steps.
With Python and pip in place, you can now install the unisos.mmwsIcm package.
All needed dependencies will be installed by just doing that.
In the OAuth model, to invoke operations, the invoker needs to present tokens that the performer expects.
“Web Services Validation Tools”, includes facilities that provide for obtaining oauth2 tokens.
Typically, the swagger specification includes a section such as:
By presentating its credentials to the token service at the “tokenUrl” RO-SAP, the invoker receives a token that it can then use in future invocations.
Obtaining of an oauth token for a given “serviceName” requires the following:
Use of the oauth2 tokens involves the following steps:
The utility that facilitates invoker’s credentials storage and that facilitates obtaining of tokens is: getTokenWithCryptKeyring-svc.py.
The invoker uses the keyring to store accessKey and secretKey for serviceName.
We encrypt the password (secretKey) in the keyring. For this, the interfaces to the keyring needs to be initialized (prepared). This is a one time activity. This preparartion involves:
Storing the invoker credentials in the keyring involves:
The following parameters:
need to be customized for getTokenWithCryptKeyring-svc.py.
Obatining the token for the serviceName and accessKey then involves:
The token is then stored in a file called current.token.
Upon installation of the python packages, the relevant executable python scripts are placed in the bin directory of where Python was installed. On Windows locate the default bin directory by running: "where rinvoker.py". On Linux locate the default bin directory by running: "which -a rinvoker.py".
Now, verify that you can run the example commands against the petstore.
In https://pypi.org/project/unisos.mmwsIcm/, go through
the instruction in the sections titled:
“Binaries And Command-Line Examples”
“Remote Invoker (rinvoker-svc.py) Examples”
“Operation Scenario (opScn-svc.py) Examples”
Just run the mentioned commands and verify that you are seeing the mentioned expected outputs.
If these all work right, then you know that the Web-Services Validation Framework has been properly installed and is operational.
Complete sources are at:
https://github.com/bisos-pip/mmwsIcm
The PYPI page is at:
https://pypi.org/project/unisos.mmwsIcm
When you have a formal swagger service specification in place, use of these service validation tools can be very convenient and productive.
Simply follow the instructions that were provided for the canonical petstore and replace petstore’s service specification with your own.
Follow the documentation to build your own scenarios for service specification and use the provided framework to combine multiple scenarios to form regression tests.
You can invoke a swagger specification’s operations directlly from the command line using the rinvoker.py command.
Typically for each swagger specification you create a customized version based on rinvoker as a seed.
In the following sections we describe common features and parameters and arguments of rinvoker and its derivatives and provide rinvokerPetstore.py as an example.
rinvoker is an ICM (Interactive Command Module) and its command syntax is based on the ICM model.
The specific commands, parameters and arguments that are implemented on rinvoker are enumerated below.
rinvoker.py commands are enumerated below.
svcOpsList command digests the Service Specification (swagger-file) specified on command line as --svcSpec= parameter and produces a complete list of ALL remotely invokable commands with their corresponding --resource, --opName and url or body arguments. Applicable options, parameters and arguments are: * Parameter (Mandatory) : --svcSpec= * Parameter (Optional) : --perfSap= --headers=
rinvoker command invokes the "opName" operation at "resource" with specified arguments. Applicable options, parameters and arguments are: * Parameter (Mandatory) : --svcSpec= --resource= --opName= * Parameter (Optional) : --perfSap= --headers= * Arguments : name=value bodyStr=jsonStr
rinvoker.py parameters are enumerated below.
The swagger file as a url or as a json/yaml file is specified with the –svcSpec= parameter.
The Performer Service Access Point Address (perfSap) is specified as a URL with the –perfSap= parameter.
Additional headers (e.g., a token) can be included with the –svcSpec= parameter.
The resource to be invoked should be specified with the –resource= parameter
The operation name to be invoked should be specified with the –opName= parameter
rinvoker.py arguments are enumerated below.
rinvoker allows you to list all possible invocations based on a service specification (swagger file). For example:
rinvoker allows you to fully specify an invocation on command line. For example:
You can specify one or more invocations as a "scenario".
Scenarios are python scripts that specify operations and their arguments and expectations of results.
Scenarios allow for the results of operations to be used as arguments of future operations.
Invoke Scenarios Are pure python specification of sequence of invocations.
Invoke-Expect Scenarios Are pure python specification of sequence of invocations subject to preparations and post-invoke verification and reporting.
OpInvoke class allows for complete invoke specification and complete results to be fully captured.
In pure python you can specify invocation of each operation, for example:
Building on the previously mentioned Operation Specification, in pure python you can the specify Operation Expectations, for example:
preInvokeCallables(ro.Ro_OpExpectation) can include a function that initializes the DB or sleepFor1Sec.
postInvokeCallables(ro.Ro_OpExpectation) can include a function that verifies the result was as expected and then reports success or failure.
Commands drived from the opScn seed are ICMs (Interactive Command Module) and their command syntax are based on the ICM model.
opScn-seed provides the following commands and parameters:
roListInv command serially invokes the list of ro.Ro_Op() opersations specified in the loaded scenario files. roListInv displays the invocation and its results. But does not do any verifications. Applicable options, parameters and arguments are: * Parameter (Mandatory) : --load=
roListExpectations command serially invokes the list of ro.Ro_OpExpectation() specified in the loaded scenario files. roListExpectations displays the invocation and its results and additionally runs the list of preInvokeCallables and postInvokeCallables. postInvokeCallables can include functions that verify the results of the invocation were as expected. Applicable options, parameters and arguments are: * Parameter (Mandatory) : --load=
The output format is:
* ->:: Invoke Request * <-:: Invoke Response * ==:: Invoke Validation (SUCCESS or FAILURE)
Additional information for each is include with "**" tags.
This output format can then be used in outline or org-mode.
RO-Verifier framework can also be used to develop complete invoker-application in python.
Invoker-Apps development model is an extension of opScenarios facilities.
The following modules:
provide a consistent framework for Invoker-Apps development.
Part II |
The RO-Verifier has been used to validate and verify a number of Web Services based on their swagger files.
Generally speaking, uses of RO-Verifier fall into two categories:
Verifcation scenarios for the PetStore web service are maintained at:
https://github.com/bxexamples/roVerifier-petstore
A set of scripts that pass all swagger files availble at:
https://github.com/APIs-guru/openapi-directory
through the rinvoker.py are available at:
https://github.com/bxexamples